Every once in a while you notice that your hard drive is working extra hard for what seems like no reason. A background process has taken your hard drive hostage, forcing it to thrash loudly as it struggles to keep up with the high rate of reads and writes. Your computer responds slowly as the process overloads the physical limitations of your drive. What are you to do?
The solution is simple, identify and stop the process that is killing your drive. There are two methods and tools that you can use to identify the process. Once you have identified the bad process, you can kill it in Task Manager.
Method 1
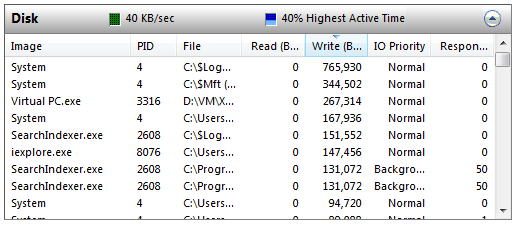
- Click on the Start Button and key in perfmon.exe /res and hit Enter. This should launch the Resource Monitor on Windows 7 and Windows Vista.
- On the overview screen click on the Disk section down arrow to see a list of all processes and the files they are writing or reading from your drives.
- Click on the Read, Write or Total headings to sort all disk operations to identify which process and file is currently using the disk the most.
Method 2
- Visit Microsoft’s Sysinternals web site and download Process Explorer.
- After you have started Process Explorer, click on the View menubar item and then Select Columns.
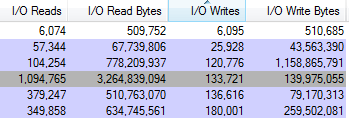
- Click on the Process I/O tab and check:
- Reads
- Read Bytes
- Writes
- Write Bytes
- Hit OK.
- You will now see the new columns listed for each process. To identify what process is killing your hard drive, just look for the process with the highest number of Reads or Bytes.