br>How do I edit the registry?
Excluding POLICY.POL for the moment, you cannot simply open SYSTEM.DAT or USER.DAT to edit the registry. You must use the correct tool for the job. Everything you do on the PC will affect the registry in some way or another, either automatically, or by you performing some action with software.
The Control Panel applets offer a simple interface between the user and most of the hardware settings stored in the registry (such as Display properties, or Modem and Network properties). Tweak UI (part of the Microsoft Powertoys set) is a special utility designed to edit various registry settings that are otherwise unavailable via the Control Panel. Policy Editor (which we'll discuss in more detail later), is more suited to administrative registry editing. Plus there are any number of tweaking utilities that "expose" the registry's commonest entries.
Since this discussion is about the registry itself, we must use a tool that allows us to edit ALL of the registry. In this case, the correct tool is the Registry Editor. By default, Registry Editor is located in the C:\WINDOWS folder and goes by the name REGEDIT.EXE.
Before continuing, a word of warning: everything you do in RegEdit is "live". That is, all edits are made there and then - there is no apply or undo button. Therefore, use extreme caution while using RegEdit and don't change anything unless you are 100% sure of what it is your editing, and more importantly, why you are editing it. The registry isn't as fragile as some would have you believe, however, if you don't know what you're doing, you can easily end up breaking Windows. However, as we'll see, it is easy to save sections of the registry before editing them.
NOTE: Your administrator may have blocked your access to RegEdit. This is a wise precaution on his/her part, since you could easily ruin their day.
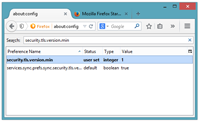
Figure 1: The Registry Editor
As you can see in figure 1, RegEdit looks very much like a Windows Explorer view, but instead of folders and sub-folders, we have keys and sub-keys, and instead of named files containing data, we have named values containing data. The data may be an ordinary text string, or a numeric value in decimal, hexadecimal or binary. In fact, the registry is so flexible it'll support 12 different types of data (compared to the one string data type available in the old INI files).
Keys always which begin with "HKEY_". The 6 listed keys are the root keys - or nodes (HKEY actually means key handle, bizarrely). Some HKEYs (like HKEY_CLASSES_ROOT) are merely pointers to sub-keys contained in one of the other HKEYs - very much like a shortcut. By creating pointers like this, access to often-used areas of SYSTEM.DAT and USER.DAT become that much quicker. Very much like creating a shortcut to a file or folder on your desktop to speed up access to it. However, unlike shortcuts, you cannot create your own pointers.
Below each of these keys there are sub-keys (much like sub-folders). When we address a key we use the familiar path convention we use when addressing a file or folder. For example, the current user's software key is addressed HKEY_CURRENT_USER\Software. HKEY_CURRENT_USER itself is actually a shortcut to HKEY_USERS, where is the current user's username.
By addressing each key by its node path, the registry can be accessed extremely quickly (just as afile is accessed quickly when you tell Windows where it is located). If you've ever used the Windows Find, Files or Folders utility, you'll know how slow it can be to find the files you're looking for. Similarly with RegEdit's Edit > Find tool. So whenever possible, narrow your search to a particular node or sub-key, and be as specific as possible.
Let's look at each HKEY node in more detail:
HKEY_CLASSES_ROOT
Often expressed as HKCR, this area of the registry is a pointer to the HKEY_LOCAL_MACHINE\Software\CLASSES key, and contains everything from filetype associations to shell extensions. Since this area of the registry is accessed every time you open a file or use an object, creating a pointer to it speeds up access to it. Also, since it is a pointer, every edit made to this portion of the registry using RegEdit is immediately reflected in the HKLM key it refers to.
HKEY_CURRENT_CONFIG
Often expressed as HKCC, this key contains all the Plug and Play settings and information about the current configuration of a multi-configuration computer (such as a docking station). This key is actually a pointer to one of the configuration branches of HKEY_LOCAL_MACHINE\Config.
HKEY_CURRENT_USER
Often expressed as HKCU, this area of the registry contains user-specific settings, and points to the user's specific branch of the HKEY_USERS key.
HKEY_DYN_DATA
Often expressed as HKDD, dynamic data which is stored in RAM (and is therefore under constant change) is stored in this key. This information can change as devices are added or removed. Device Manager uses this data to show the current hardware configuration, and is used to constantly update System Monitor. This key doesn't actually exist in the registry files, it only exists in RAM.
HKEY_LOCAL_MACHINE
Often expressed as HKLM, this key contains machine-specific information about the hardware installed, as well as software settings. The information in this key is used by all users who log on to the machine.
HKEY_USERS
Often expressed as HKU, this key contains information regarding the default and current users. Each user who logs on has a sub-key under this key, and is made up from their own USER.DAT file. If you find a particular user is missing from this key, log on to their profile and export their from this key. Log on under all other users, including the default user, and import their .
REG files
If you highlight a key and select File > Export, you will be asked to enter a filename. The end result is a .REG file which contains all the entries in and below the key you highlighted. You can even backup the entire registry by this method. However normally you'd use it to quickly backup a key you were about to remove or edit.
REG files are nothing more than plain-text files. The REG extension is associated with RegEdit so double-clicking a REG file will allow you to "merge" (import) the data contained therein - thus restoring the entries to what they were before you edited them. However, there are is one drawback: new entries added since the REG file was created will not be removed - only existing entries are overwritten, and missing entries restored. However, for most edits this is perfectly adequate.
The REG file format is relatively simple. Take a look at the Registry Hacks page for some examples. At the very top of the file is the identifier, REGEDIT4. This must appear at the top of all REG files on a line of its own. Below this are two blank lines (although one is sufficient) followed by the first key, which is surrounded by square braces []. If there are any data values for this key, they are listed immediately below it in "data name"="data value" format (for string data types). Other data types have their own specific format, with the type of data immediately following the equals sign (=), e.g., "data name"=hex:00000001 for an 8-bit binary value, and "data name"=dword:00,00,00,00 for double-word values (4 bytes).
Every key has a default value. However, not all default values actually contain data (they are not set). But since the default value has no name (the name is actually the name of the key it belongs), the "@" symbol is used instead. The default value is always a string type so, whenever one is set, the REG file will show an entry like @="default value". One such use for a default value is to specify a default key immediately below the default value's key. We'll look at this in greater detail shortly.
After all values for a particular key are listed, a blank line separates it from the next key. Notice how keys are listed in hierarchical form, from the parents to the children. This is because missing keys need to be recreated, and this can only be achieved if the parent key(s) exist. Keys are added (if missing) in the order they appear, thus parents must always appear before their children. However, the order of the parents at similar levels may not be alphabetical, and the values themselves may not be alphabetical either. The order they appear in is the order they were created in. You could spend time sorting the order but there's very little point in doing so. A particular key or value will be found just as quickly regardless of its order.
The REG file continues in this fashion, listing keys and their respective values, separating each key with a blank line. At the end of the file there must be at least one blank line (this is common of most script files - since the carriage return/line-feed at the end of each line is treated as a part of the line).
The observant amongst you may have noticed file and folder pathnames in the data values use double-forward-slashes ("\") rather than the normal single-forward-slash (""). This is simply because the single forward-slash is a special "tag" character, used to clarify the character that follows it. In other words, the two characters are treated as a single character. For example, "\t" translates as a tab character, while "\n" translates as a carriage-return/line-feed. Since the forward-slash is a special character, it can't be used in registry pathnames. However, a double-forward-slash clarifies that the second forward-slash is a genuine forward-slash. The first is therefore ignored. If you look in the registry you'll see the double-slashes are correctly shown as single-slashes.
If you've looked through my Registry Hacks you may have discovered one or two you'd like to try. Now would be a good opportunity to put your newly found skills into action, while you observe the REG inserting its entries. Simply use RegEdit to navigate to the appropriate key that the REG will edit, and look at the current entries. Merge the REG file (by double-clicking it) then hit F5 to refresh RegEdit. Your new entries will appear in the editor. Note that some settings (local machine settings in particular) will require a reboot to take full effect. These types of settings are read at bootup and remain in memory throughout. Others (particularly current user settings) may require a logoff in order to take effect. However, for the most part, settings will take effect from the moment you merge them - although the program that uses those settings may require refreshing itself (or even to be shut down and re-run) before the settings take effect. If in doubt, reboot.
A few paragraphs ago I mentioned that REG files couldn't remove new entries added since making the REG file. That isn't entirely true. To remove entries using REG files you need to remove the entire key the entry appears in, and then restore the other entries. For example, suppose I have a key for my own software (HKEY_LOCAL_MACHINE\Software\PCForrest) and want to remove the data value named "MyApp". I would first export the [HKEY_LOCAL_MACHINE\Software\PCForrest] key, and then move the "MyApp" line to the top of the file, under the same key but with a leading minus (-), like so:
REGEDIT4
[-HKEY_LOCAL_MACHINE\Software\PCForrest]
"MyApp"="This Entry Should be Removed"
[HKEY_LOCAL_MACHINE\Software\PCForrest]
"ThisApp"="This Entry Belongs Here"
"ThatApp"="This Entry Also Belongs Here"
Note that when removing keys, it doesn't matter what values you place below them. I include them merely to show precisely what I want to delete. However, be aware that any values in addition to the ones in this file (and any sub-keys within it) will also be deleted.