Anytime your network refuses to send and receive data properly , your first troubleshooting step should be to check fof problems with the physical connection between the local computer and the rest of the network. Assuming your network connection uses the TCP/IP protocol , your most potent weapon is the Ping ulity. When you use the Ping command with no parameters , Windows sends four echo datagrams , small Internet Control Message Protocol (ICMP) packets, to the address you specify. If the machine at the other end of the connection replies, you know that the network connection between the two points is alive.
To use the Ping command , open a Windows command prompt window (Cmd.exe in Windows XP) and tape the command ping target_name (where target_name is an IP address or the name of another host machine ).
If all the packets you send come back properly in roughly the same time , your TCP/IP connection is fine and you can focus your troubleshooting efforts elsewhere.
Enjoy !

If you own a Google Chromecast streaming device, you can easily share a browser tab in Chrome browser or even your entire desktop. This can be very useful when presenting from your laptop or if you just want to watch something on a big screen that is only on your PC. The only requirement is you must be on the same network as your Chromecast...
Read More
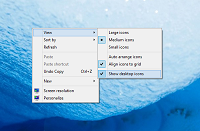
If you are a fan of minimalist desktop experiences, hiding the desktop icons are an easy way to clean up the Windows interface. Instead of saving everything to your desktop, use the default profile folders such as downloads and documents. Actually hiding all the icons on your desktop is a very simple customization hidden in the right-click context menu. Just right-click on the desktop, select View...
Read More
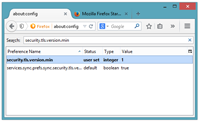
Google security researchers have published details about a major security flaw found in the SSL protocol that is used to encrypt data transferred between your browser and a web server. SSL is typically used in situations where logon credentials are validated...
Read More
Enabling two-factor authentication is a great way to add an additional level of protection to your Microsoft account. Even if your password is stolen, your account is still protected because two-factor authetication requires an additional level of verification to log in. Microsoft calls their version of two-factor authentication "two-step verification" and it works by providing you with a random code...
Read More


