In my last article I showed you how you can protect your computer against anonymous user account attacks by turning on account logon auditing so you could see when someone attempts to remotely logon to your account. Now I am going to help your increase your level of protection with the Account Lockout Policy.
Creating an Account Lockout Policy will protect your account by limiting the number of time a remote application or attacker can try to guess your password. This works by automatically locking out your account after a designated number of incorrect passwords were entered. Your account will remain locked out for a designated period of time before it is automatically unlocked and it can be logged into again. This provides a valuable addition to your account security because it can render brute force password attacks useless. If you have your lockout threshold set to 4 bad attempts and the lockout duration to 15 minutes, an attacker can try to guess your password a maximum of 16 times per hour.
Now that you know how valuable an Account Lockout Policy is, let’s get it setup on your computer:
- Click on the Start Button and key in Secpol.msc and hit Enter.
- Navigate through Account Policies and Account Lockout Policy.
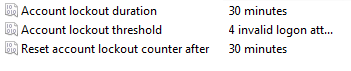
- Right click on Account lockout threshold and select Properties.
- Enter in the value you want to use and hit OK to save. I like to use 4 here.
- Windows will set the default values for the lockout duration and Reset account lockout counter values. If you want to change these values from the defaults (30 minutes), right click on them and select Properties. After making your changes hit OK to save and exit.
 The Adobe download manager is part of the normal install of Adobe Reader and Flash that allows Adobe to bundle additional software with their products. After the download manager is installed, Reader/Flash along with other software (Adobe Air) can be downloaded and installed. When dial-up Internet connections where common download managers provided a valuable...
The Adobe download manager is part of the normal install of Adobe Reader and Flash that allows Adobe to bundle additional software with their products. After the download manager is installed, Reader/Flash along with other software (Adobe Air) can be downloaded and installed. When dial-up Internet connections where common download managers provided a valuable...