Ever wonder why you get network authentication errors when you are trying access a mapped network share from a process that was elevated with UAC? That is because each administrative account, starting with Windows Vista and newer, runs with two security tokens. One with low rights that is the default and then the administrative level token. When you run something as administrator or change a setting that requires the UAC prompt, your token is switched and runs the action under that context.
Network drives that were mapped under the default low rights context token are naturally not available to other tokens which is why you get authentication errors. The workaround is to apply a registry tweak that allows the local security authority to use all tokens currently assigned to the logged in user and access a network connection with any that work.
- Open Registry Editor by typing in regedit on the Start Menu and hitting Enter.
- Navigate through HKEY_LOCAL_MACHINE, Software, Microsoft, Windows, CurrentVersion, Policies and System.
- Right click on System and select New and then DWORD value.
- Enter EnabledLinkedConnections as the name.
- Right click on the new EnabledLinkedConnections and select Modify.
- Set the value to 1 and click OK.
- Reboot your PC.

If you own a Google Chromecast streaming device, you can easily share a browser tab in Chrome browser or even your entire desktop. This can be very useful when presenting from your laptop or if you just want to watch something on a big screen that is only on your PC. The only requirement is you must be on the same network as your Chromecast...
Read More
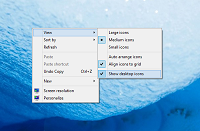
If you are a fan of minimalist desktop experiences, hiding the desktop icons are an easy way to clean up the Windows interface. Instead of saving everything to your desktop, use the default profile folders such as downloads and documents. Actually hiding all the icons on your desktop is a very simple customization hidden in the right-click context menu. Just right-click on the desktop, select View...
Read More
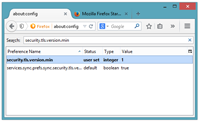
Google security researchers have published details about a major security flaw found in the SSL protocol that is used to encrypt data transferred between your browser and a web server. SSL is typically used in situations where logon credentials are validated...
Read More
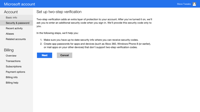
Enabling two-factor authentication is a great way to add an additional level of protection to your Microsoft account. Even if your password is stolen, your account is still protected because two-factor authetication requires an additional level of verification to log in. Microsoft calls their version of two-factor authentication "two-step verification" and it works by providing you with a random code...
Read More


